Android security step #9: Assess your password management system
Google’s password manager is better than nothing, but you’ll get stronger security assurances, more advanced and useful features, and broader support for in-app password filling by using a dedicated password management service.
We’ve got some commendable Android password manager choices, too, with my own current recommendations revolving around 1Password for most people and Bitwarden for anyone who needs a free path or prefers a self-hosted setup. Both services work equally well on the desktop front and even on iOS, with the main differences revolving around cost, extra features, interfaces, and the resulting overall user experiences.
If you aren’t using one of those services, now’s the time to start. And if you are already using such a service, take a few minutes now to peek into the app’s settings and make sure you’re taking advantage of all the on-device protection it offers. With 1Password, for example, you should confirm that the app is set to be protected by either biometric security or a password and that it’s configured to automatically lock within a few minutes after you stop using it. The app can also automatically clear your system clipboard of any passwords you copy after 90 seconds, which is a smart pinch of added protection to have. (All of those options are in the Security section of 1Password’s settings.)
Like Google, most good password managers also now provide an option to analyze all of your passwords and identify any that would be advisable to change — ones that are duplicated or otherwise not as strong as they could be. That’s another smart thing to check up on as part of this annual audit.
Android security step #10: Evaluate your two-factor authentication situation
A single password isn’t enough to protect an important account these days — especially one as wide-reaching and valuable as your Google account. Two-factor authentication makes it so that you have to either confirm the sign-in on an approved physical device or put in a special time-sensitive code in addition to your password anytime you try to sign in. That significantly increases your level of security and decreases the odds of anyone ever being able to break in and access your personal data, since they’d need both knowledge of your password and the physical presence of your key-like device to do it.
If you don’t yet have two-factor authentication enabled for your Google account, head over to this site to get started. And don’t stop with just Google, either: Look into enabling two-factor authentication on any service that offers it, including your password manager, your social media accounts, and any non-Google cloud storage services that you use.
If you really want to keep your account secure, Google also offers a souped-up option called Advanced Protection. It requires you to purchase physical security keys and then use those anytime you sign into your Google account. It also severely limits the ways in which third-party apps can connect to your account. That sort of elevated and locked-down setup probably won’t be sensible for most folks, but if you feel like you need the extra protection, you can learn more and enroll here.
Android security step #11: Optimize your lock screen security
Your lock screen is the guard of your Android device’s gate — and there are a few things you can do to beef up its muscle and make sure it’s fully prepared for the job.
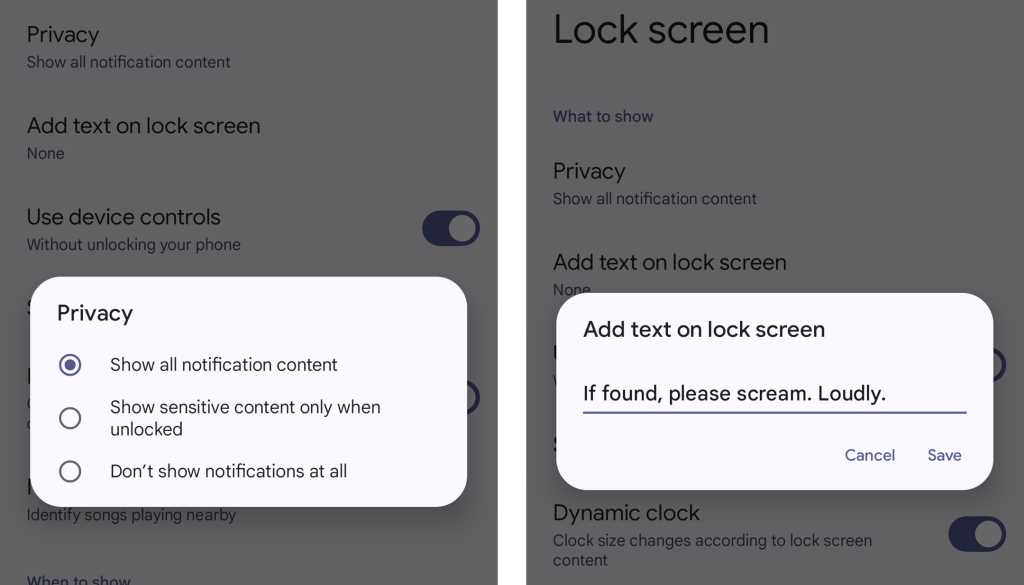
First, think about the types of notifications you get and how much of that info you want to be visible on your lock screen — since anyone who gets their hands on your phone could easily see all that data. If you tend to get sensitive messages or just want to step up your security and privacy game a notch, head into the Display section of your system settings and select “Lock screen” — or, if you’re using a Samsung phone, look in the separate Lock Screen section of your system settings instead.
There, you’ll find tools for controlling precisely what will and won’t be shown in that pre-authentication area as well as for creating a security-minded message that’ll always appear on your lock screen — for instance, something like: “If found, please call Joe T. Schmo at 333-222-1111.” You could even consider adding an emergency contact into your settings and then using the lock screen message to direct people to that information.
JR Raphael, IDG
And finally, provided your phone is running Android 9 or higher, an option called lockdown mode is well worth your while to activate or just remind yourself about. Lockdown mode gives you a fast way to lock your phone down from all biometric and Smart Lock/Extend Unlock security options — meaning only a pattern, PIN, or password could get a person past your lock screen and into your device.
The idea is that if you were ever in a situation where you thought you might be forced to unlock your phone with your fingerprint or face — be it by some sort of law enforcement agent or just by a regular ol’ hooligan — you could activate the lockdown mode and know your data couldn’t be accessed without your explicit permission. Even notifications won’t show up on your lock screen when that mode is activated, and that heightened level of protection will remain in place until you manually unlock your phone (even if the device is restarted).
There’s just one catch: On some devices — including Samsung phones — it’s up to you to enable the option ahead of time in order for it to be available. But doing so takes only a couple of seconds: Search your system settings for lockdown and then look for the toggle to enable it. (If you don’t see any such option at all, odds are, you’re using a Google Pixel phone and/or a recent enough Android version that it’s just on and enabled by default.)
Then, if the need ever arises, remember this: In your phone’s power menu, along with the regular options for restarting and shutting down your device, you’ll always find a button to activate that “Lockdown” function. Hopefully, you’ll never need it — but now you’re ready in case you do.
And with that, guess what? You’re more than halfway done with this annual checkup. Not too painful so far, right? Only seven more steps to go…
Part III: Device access
Android security step #12: Clean up your list of connected devices
Anytime you sign into a new device with your Google account — be it an Android phone, a Chromebook, or even just the Chrome browser on a regular PC — that device is added to an approved-for-access list and associated with your account.
Click over to this page in Google’s security settings and give your list a once-over. If you see any old devices you no longer use, click on ’em and then click the “Sign Out” button that pops up to make sure they no longer have access to your account. And if you see any devices you’ve never used, remove ’em right away — and then go change your Google account password immediately.
Android security step #13: Clean up your devices in the Play Store
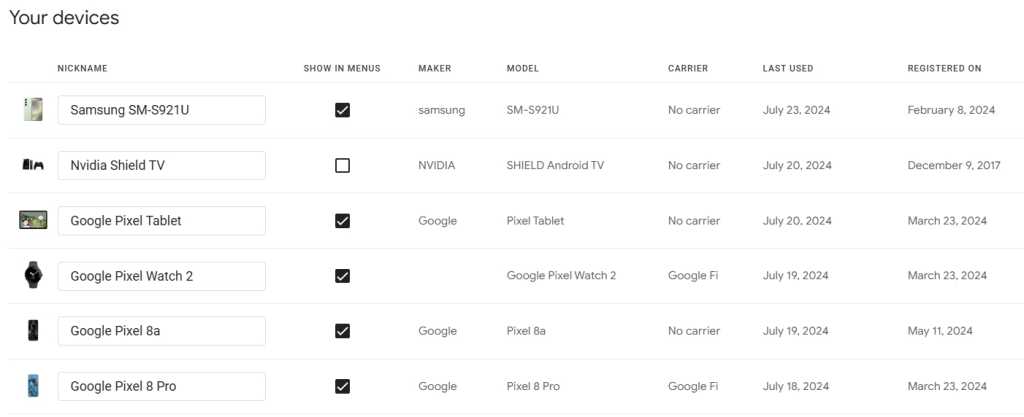
This one isn’t directly related to security, but it’s a good bit of housekeeping to perform while you’ve got your cleaning hat on: Head over to the Google Play Store Devices tab and look at your list of available devices. These are the devices that show up as options every time you install a new app from the Play Store web interface — and also the devices that show up as options in Google’s Find My Device utility (more on that in a sec).
Go ahead and uncheck the box next to “Show in menus” for any devices you no longer use. And if you see any devices with cryptic codenames, click the “Edit” button alongside ’em and rename ’em to something you’ll recognize.
JR Raphael, IDG
The next time you download an app or remotely locate one of your devices will be a much smoother experience as a result.
Android security step #14: Make sure your device is prepared for the worst
Speaking of remote location, you might not realize it, but Google has its own utility for tracking, finding, and remotely wiping an Android device in case you ever lose it — and the whole system is built right into the operating system.
So what are you waiting for? Make sure all of your phones, tablets, and other associated devices are enrolled now, before it’s too late. Just follow my quick ‘n’ simple Find My Device setup instructions for any device you’ve got on or around ye.
Now bookmark the web version of Find My Device and/or download the app on a Chromebook or any other Android-compatible device you own. If you ever can’t find any of your devices, open the service — and you’ll be able to pinpoint precisely where the missing gadget was last seen. You can also force most phones or tablets to ring as well as remotely lock or erase ’em entirely.
Android security step #15: Think about whether you should be using a VPN
No matter how secure your Android phone itself is, someone could theoretically still snoop on your sensitive info if you’re transmitting it over an insecure network. That’s where virtual private networks, or VPNs, come into play: They encrypt all of your incoming and outgoing data so that no one could intercept it and see what you’re doing at the network level.
VPNs aren’t something everyone needs to worry about, but if you use your phone for a fair amount of business work or with any other type of sensitive material, it’s something you ought to at the very least consider — particularly if you use a lot of open Wi-Fi networks, where snooping can be a genuine concern (at least, in scenarios where a site or service’s traffic isn’t already encrypted).
So where to start? Well, first, some companies provide their own custom VPN services for employees. If that’s the case for you, congratulations! You’re already all set.
If you’re using the Google Fi wireless service, the answer is similarly simple: Fi now provides an option to automatically encrypt all of your network connections via Google’s VPN service. All you’ve gotta do is activate it.
The same goes for Pixel phones, which come with Google’s own VPN service as a free and readily available option.
Otherwise, you’ll have to turn to a third-party Android VPN service in order to gain that added level of protection.
Part IV: Big-picture thinking
Android security step #16: Make sure you’ve done your virtual estate planning
We’ve got one more bit of “what if” preparation to address — and it’s slightly unpleasant to think about: If something bad were ever to happen to you, would you want someone else to be able to access your Google account and all the data associated with your devices? With a company-controlled account, it’s less of a worry. But if you’re using a personal Google account and/or maintaining your own Workspace setup for a small business, you don’t want to let that go unaddressed. Take a moment to prepare for the possibility now, and it’ll make things infinitely easier for your friends or loved ones in the event that you ever develop a mild case of, erm, death.
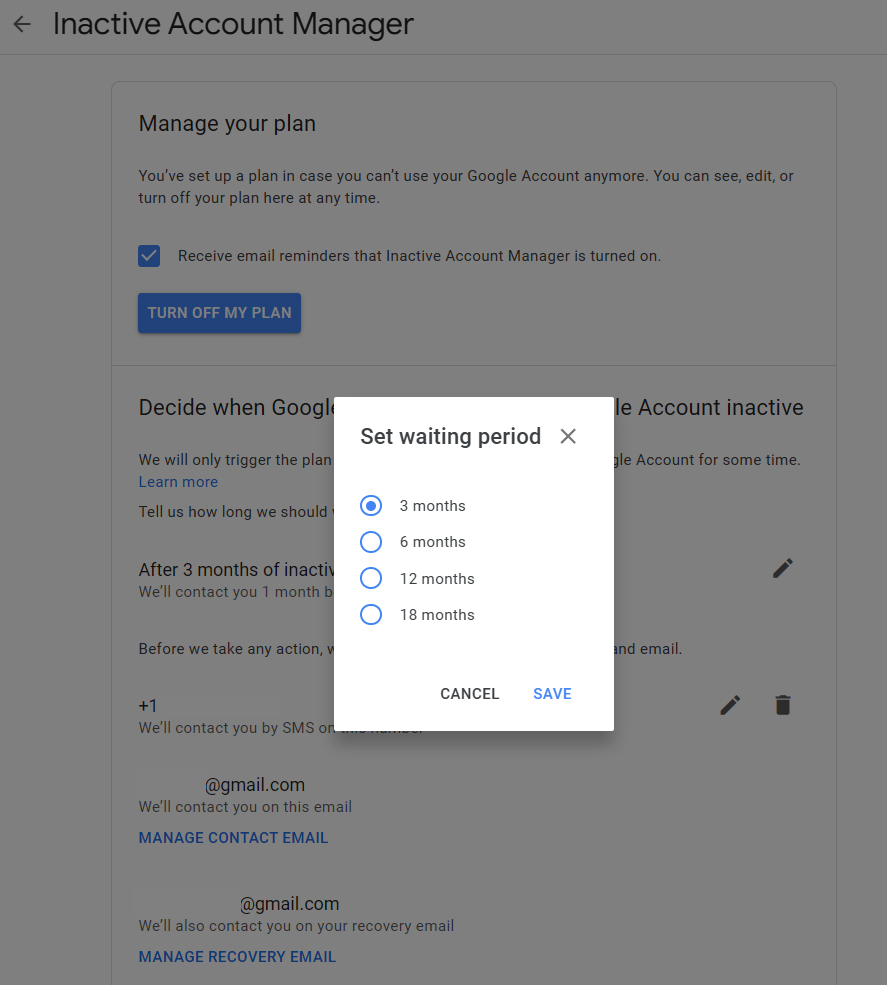
It’s actually pretty painless to do (the preparation, that is — not the death): Just go to this page and make sure you’ve set up Google’s Inactive Account Manager. That system detects when your account has been inactive for a certain period of time — three months, six months, a year, or a year and a half, depending on your preference — and then notifies a trusted contact of your choosing and provides them with whatever level of access you want. You can even set up an auto-reply to kick in for your Gmail (creepy!), and you can tell Google to delete a personal account altogether after a specific amount of time has passed.
Inactive Account Manager is designed to be extraordinarily cautious, with numerous fail-safes in place — including an option to try to contact you via SMS and email a month before your inactivity plan goes into action.
JR Raphael, IDG
Some other services, including 1Password, offer similar systems for setting up emergency access to your account in an extreme situation. There’s also a clever free (and open source!) service called WeExpire that lets you create secure dockets of info that can be shared via QR code in a similar sort of way.
It’s a strange part of security to consider, but — just like with every other area we’ve discussed so far — it’s something worth thinking about and preparing for before the need arises.
Android security step #17: Perform a general Google security check to round things out
Take a deep breath: We’re almost done! This next-to-last step will take you through a broad security check that’ll look for any remaining weak points in your Google account and Android security and then prompt you to fix ’em right then and there.
Just go to this Google security site and click through any issues it presents. It’ll confirm that you’ve successfully performed some of the actions we’ve already discussed and then look for any other potential red flags or opportunities for improvement.
Consider it your confirmation that your personal security setup is A-OK.
Android security step #18: Think carefully about third-party security suites
Last but not least: Now that you’ve made sure your Android security situation is shipshape, think about any third-party security suites you’re using (whether you installed ’em yourself or they came preinstalled on your phone or tablet) and what they’re actually adding to your device.
You’ve already verified that your device is protected. Android is actively scanning for threats on several levels, both on the server side at the Play Store and on your phone as new apps arrive (from any source) and continuing over time. Plus, you’re exercising basic smarts about what apps you download. The operating system could even be looking out for phishing scams, and the Chrome Android browser is keeping an eye out for web-based threats as well.
Beyond all of that, your devices are all enrolled in a sophisticated cross-platform system for remotely tracking, pinging, and erasing as needed. And all of that is happening on the native platform level.
So given those layers, is the third-party security suite on your phone doing anything that isn’t redundant and unnecessary? It’s probably eating up system resources and impacting performance for no real reason — and quite likely also costing you money you don’t need to be spending — but is it actually accomplishing anything of value that Android itself isn’t already handling in a more direct manner?
Unless you’re relying on the app for supplementary services like added anti-theft detection and payment protection, the answer is almost certainly no. If having an extra security layer makes you feel safer, hey, do what works for you. But if you’ve completed every step of this checkup, there’s really no reason you need it — and every reason to send it packing. (To be clear, there are plenty of privacy and security apps that could be worth your while; they just aren’t the silly, bloated device-scanning suites that are so popular among folks who don’t know better.)
And with that, my fellow Android-adoring security-seeker, your checkup is complete. All that’s left is to set yourself a reminder to revisit these same steps this time next year. The areas we’ve just covered are constantly evolving, and giving yourself an annual once-over is the best way to ensure you’re always in tip-top shape.
Get six full days of advanced Android knowledge with my free Android Shortcut Supercourse. You’ll learn tons of time-saving tricks for your phone!

